For some time now, organizations around the globe have been met with looming cybersecurity threats, increased pressure from stakeholders, and catastrophic internal IT Security fatigue. As a result, one of the most in-demand leadership positions is the Chief Information Security Officer. Just like numerous other “as a service” platforms, the rise of “CISO as a Service” or Virtual CISO (vCISO) has also become a major game-changer for emerging and medium-sized businesses, allowing them to gain the same cybersecurity direction as a large enterprise, but at a fraction of the cost.
vCISOs provide traditional cybersecurity leadership through a pre-defined or on-demand plan. Selecting a vCISO can certainly be an intimidating endeavor as many security providers claim to have “cutting-edge” services. In this article we highlight the 5 characteristics we uphold should be on your vCISO qualities wishlist:
- Real Cybersecurity Experience
- Creates Cybersecurity Risk and Vulnerability Objectives
- Speaks the Business Language
- Understands Compliance/Quick to Adapt
- Provides Appropriate Solutions
Real Cybersecurity Experience
This one might sound like a no-brainer but we caution you to examine the credentials of corporate cybersecurity service providers claiming to be the “best” at what they do. This is understandably vital at a time when new cybersecurity service companies are springing up ubiquitously to take advantage of the demand and subsequently available capital. At the time of writing this “virtual ciso” and “cyber security risk management” are trending lookups on Google. We can expect this inclination to continue to climb.
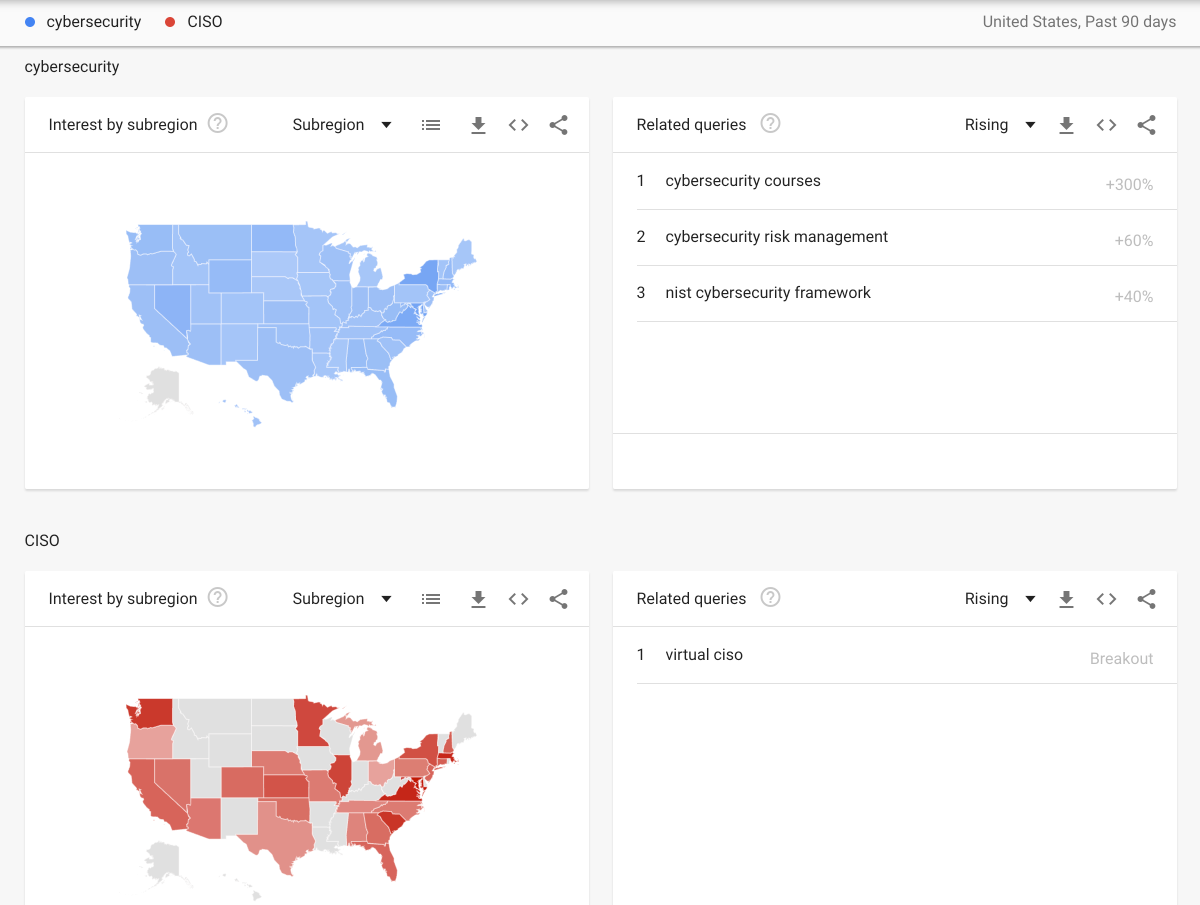
Unfortunately, we can also expect that not every cybersecurity services company will be equipped with the same expertise. Security is a broad discipline that is as vast and deep as the ocean. As such, your vCISO will need to understand a range of technical concepts like networking, cloud, and cryptography at a high level.
Some of the ways Silent Sector demonstrates expertise as a Cybersecurity Service Provider and Virtual CISO are:
- Leadership possesses professional certifications like CISSP, CRISC, OSCP, etc.- Has you vCISO taken the time to formalize their experience?
- Publishing an international bestselling cybersecurity book, “Cyber Rants.” This book exposes the truths of corporate cybersecurity programs – is your vCISO conscious of proven industry best practices, myths, and the attributes of a successful cybersecurity program?
- Partnerships with other highly respected firms like Arizona’s largest locally-owned CPA firm – does your vCISO have healthy relationships with industry auditing firms?
- Weekly podcasts covering threat patterns and adversary tactics across a variety of industries – is your cybersecurity consultant on the hunt for tomorrow’s threats?
- Personnel spotlights in journals like Authority Magazine – Is your vCISO recognized as a security connoisseur?
- Extensive military special operations and Fortune 500 backgrounds – We understand the criticality of completing projects on time, on budget, and most importantly without impeding your business mission.
Creates Cybersecurity Risk and Vulnerability Objectives
A well-informed vCISO understands that Threats x Vulnerabilities = Risk. Vulnerabilities are essentially gaps in your network security. For your organization to maintain its reputation, shareholder trust, and other operational targets- a risk assessment program is a must. This is why one of the key initiatives any prospective vCISO should offer or improve on is your Risk Management strategy.
A risk management program is the most effective way to improve the likelihood your organization is prepared for the day when you are targeted. A formalized risk management program is also required because we live in a world where risk is never 100% eliminative and threats are constantly changing.
Speaks the Business Language
Be wary of virtual CISO consulting services boasting of their lengthy cybersecurity portfolio and previous projects without addressing how they improved the business overall. Successful vCISOs understand cybersecurity achievements are the result of a group effort and subsequently enhance the business.
Another trait to look for when selecting a vCISO is how effectively they interact within your organization. An exceptional vCISO can articulate deep technological concepts into statements that demonstrate “the why behind the what” in regards to technology choices. It is also worth noting your vCISO should be somewhat positive or energetic in a way that empowers your personnel to be excited about cybersecurity rather than use scare tactics. This is particularly obligatory since your vCISO will communicate with key stakeholders, in-house IT staff, 3rd party auditors, potential clients, etc.
Understands Compliance/Quick to Adapt
Cybersecurity consultants work for a plethora of organizations in distinct industries and geographic locations. The intricacies between industries require a vCISO service organization to be adaptable. For instance, keeping up to date with rapidly changing legal, regulatory and industry regulations could be a full-time role in itself. Also, given that the threat landscape is entirely virtual, cybersecurity consultants must fend against domestic and international threats. Unlike traditional occupations which have a lot of foundation, a lot of cybersecurity services rely on the managed services provider to take the initiative and soak up security best practices or industry regulations. The vCISO must be a dependable source for cybersecurity intelligence as it pertains to your business, its missions, and industry forecast.
Compliance goes hand in hand with security as it helps prevent and detect violations of rules or security best practices. Your vCISO should be mindful of how compliance with SOC 2, PCI-DSS, and HIPAA enhances public relations, reduces legal risks, while also improving operational efficiency. Does Your vCISO demonstrate a history of being a self-starter, ambitious learner, and able to work under minimal direction?
Image via Security Engineer @Swagitda
Provides Appropriate Solutions
Cybersecurity service providers often incorporate buzz words to help market their services and become more favorable by search engines. Your vCISO provider might offer to deploy impressive-sounding tools and nice looking dashboards. However, much of information security can be attributed to basic routine changes that take advantage of existing workflows. For instance, basics such as enabling multi-factor authentication or removing local admin rights for standard users has a much more significant impact for most mid-market and emerging companies than deploying an expensive Security Information and Event Management tool that uses machine learning. Silent Sector is keen on leveraging your current resources rather than spend capital on implementing, tuning, and maintaining new products unless they will offer significant returns.
At Silent Sector, we understand that security’s main goal is to support the business and not hinder it. Does your prospective vCISO highlight the cooperative relationship between security and business accessibility? Interested to learn more about improving a company and its bottom-line with cybersecurity? Contact us to learn more.


