Government contractors today are constantly under the scrutiny of security compliance. After all, breaching a government contractor is an efficient path to stealing valuable U.S economic as well as national security information. These attaches are actively carried out by nation-state threat actors. Several years ago, the Department of Defense (DoD) worked with the National Institute of Standards and Technology (NIST) to create a security manual to address this issue- it was titled NIST SP 800-171. However, implementing NIST SP 800-171 has proved difficult as fulfilling its requirement can be costly and almost unattainable for contractors with low cyber literacy. This year the Cybersecurity Maturity Model Certification (CMMC) was released to revamp the existing requirements for DoD contractors and help address the complications associated with NIST SP 800-171.
What is NIST SP 800-171?
First, let’s quickly revisit NIST SP 800-171. In October 2016, the Defense Federal Acquisition Regulation Supplement 252.204-7012 (DFARS 7012) was released and became mandatory for government contractors. It stated that all contracting companies preparing to or already conducting work with the federal government needed to comply with the 110 controls in NIST SP 800-171. This is still upheld today, and if you have bid or are bidding on a contract with this clause your organization is obligated to comply with NIST 800-171. While there is no formal certification requirement under NIST SP 800-171, at any time your company should be prepared to provide its System Security Plan (SSP). 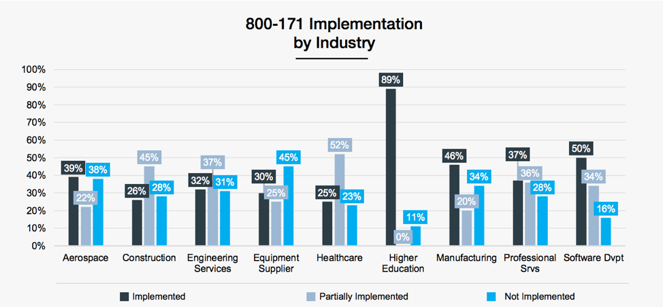
Image by Cyber Crime Magazine
Why do I need to seek CMMC compliance, what is wrong with NIST SP 800-171?
SSP was initially developed as a self-certifying honor system. Unfortunately, contractors started to falsify their SSPs and it is estimated that 45% of small and medium-sized defense contractors haven’t even read NIST SP 800-171 despite it being a requirement since 2016. In response to the growing concerns of cyber-attacks, the government developed the CMMC. The CMMC requires compliance with a fundamental set of security controls and 3rd part attestation from a certified 3rd party assessment organization (C3PAO). C3PAO’s are supposed to have CMMC trained assessors to conduct certification audits. The CMMC Accreditation Board (CMMC CAB) will publish a list of C3PAOs of companies who have successfully completed the training. As of December 13th, there are no C3PAO organizations (official site cmmcab.org click marketplace>C3PAOP) who are certified to conduct CMMC certifications. COVID-19 has significantly delayed the authorization of C3PAOs.
DFARS 7012 does not mention CMMC, but a new interim rule in DFARS Clause 252.204-7021 was released September 29, 2020 and is set to be enforced November 30, 2020. The interim rule implements the CMMC for DoD contractors but also requires contractors to conduct and report the outcome of self-attestations of the NIST SP 800-171. CMMC essentially addresses all the controls of NIST 800-171 and incorporates a few additional ones in level 4 and 5. In a previous blog, we outlined CMMC levels, but the gist is there are 5 levels of certification making it easier to phase security (most contractors are expected to land at level 3 which subsequently requires coverage of all NIST SP 800-171 controls). Contractors have until October 2025 to reach at least a level 1 CMMC certification level.
It is important to note that NIST SP 800-171 is not going away and there is nothing inherently wrong with it. CMMC just offers more protection of controlled unclassified information (information the government creates or possesses or that another organization creates or possesses on its behalf) and measures a DoD candidate/contractor’s cybersecurity maturity. CMMC levels 4 and 5 go a stride above NIST SP 800-171 because they aim to demonstrate organizations proactively protect against threats, tactics, and procedures of advanced persistent threats. They are also only valid for three years. 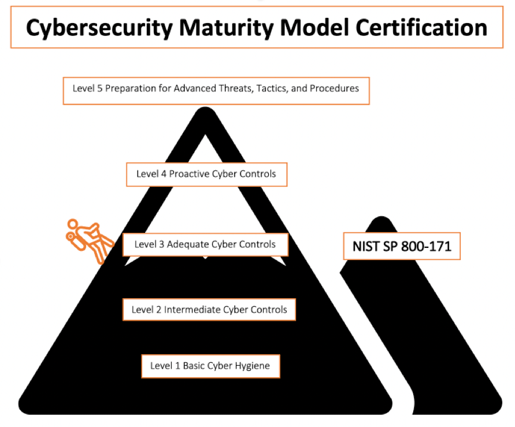
What does my organization need to do today?
If your business is a defense contractor, you should be getting prepared to comply with the CMMC interim rule and NIST SP 800-171 requirements. If you are not sure what is expected, we highly recommend hiring a compliance analyst or better yet reaching out to a 3rd party organization like Silent Sector that specializes in managed cybersecurity services. With CMMC still in its beta stage, the best preparation for it is adhering to NIST SP 800-171.
- Update NIST SP 800-171 self-assessment
- Conduct if not already executed
- Identify organizational scope and desired security maturity level.
- Handling basic CUI requires only a level one while other handling sensitive CUI may require a level 4
- Identify any SSP and milestones that may are relevant to NIST SP 800-171 and CMMC
- Look out for CMMC level requirements in RFI and RFPs as the DoD started putting CMMC in contracts September 2020
If your organization is an external service provider such as a Managed IT service provider, cloud service, etc. contractors can inherit your CMMC certification. This is excellent news as it prevents service providers from having to go through the CMMC process for each client.
- Update NIST SP 800-171 self-assessment.
- Subscribe to CMMC emails from CMMC accreditation board https://www.cmmcab.org/subscribe)
- Create compliance mapping for each client (C3PAO will validate this)
- Evidence that shows which objective is applicable in an entity’s in-scope assets and that the objective is met
- Confirm that all personnel are prepared with the new rules and ready to help
The new CMMC certification will enhance the security of not only DoD contractors but that of our nation. It is imperative contractors embrace it sooner rather than later as it will later determine whether your business can continue to offer services for the DoD. Is your organization ready for the day when CMMC becomes mandatory?


